Whoa! I was messing around with a Solana NFT drop the other day and hit a snag. Really? Yeah. My browser wouldn’t talk to the dApp. Something felt off about the permissions it asked for. My instinct said “pause”, so I stepped back and double-checked the wallet connection flow instead of rushing in. Initially I thought any wallet extension would do the job, but then I realized that subtle UI differences, permission prompts, and network settings matter a lot; they can mean the difference between a smooth trade and a costly mistake.
Browser wallets are the bridge between your browser and Solana apps. Short version: they store your keys locally and sign transactions when you approve them. They let you interact with marketplaces, games, and DeFi without running a full node. This is convenient. And risky. Hmm… seriously — convenience and risk live next-door to each other.
Okay, so check this out—before you install any extension, think like a skeptic. Who built the extension? Is the publisher verified? Do community channels and GitHub repos corroborate legitimacy? On one hand, popular wallets like Phantom have wide adoption and active audits. On the other hand, copycat extensions and fake listings are common in browser stores. Actually, wait—let me rephrase that: popularity helps, but you still must verify the publisher and the download source. Somethin’ as simple as a double-check saved me one time. Very very important.
Download only from the vendor or a verified page. For Phantom, grab the official link from the developer or a trusted landing page like this phantom wallet download extension. Don’t click an ad. Don’t open a random link in Discord. Seriously?
Step 1: Close other wallets or extensions if you have them. This reduces conflicts. Step 2: Install from the verified source. Step 3: Create a new wallet or restore from seed if you already have one. Step 4: Write your seed phrase on paper and store it off‑line. No screenshots. No cloud notes. No phone photos. Hmm… that last rule feels strict, but it’s for a reason.
When you’re prompted for a password, pick one you actually will remember but that isn’t reused elsewhere. If you use a hardware wallet, link it. Hardware devices add a very tangible security layer because the signing happens on the device, not in the browser. My advice: consider hardware for more than small sums. I’m biased, but that little extra cost buys peace of mind.
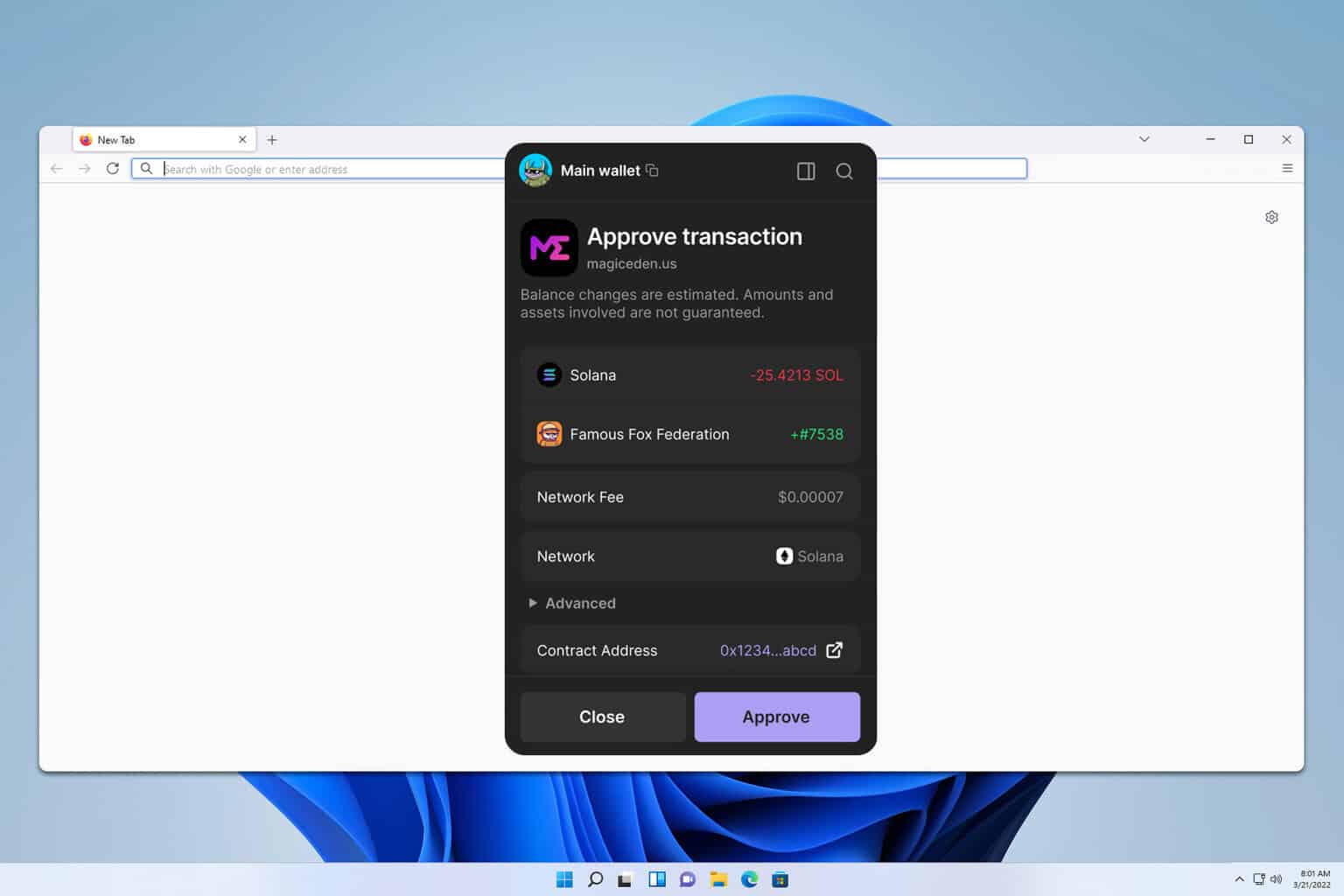
Also, the permission screen matters. Read it. If a dApp asks to “Manage your account” or “Move funds”, that’s different from a one-time signing. Approve only the actions you expect. If you’re unsure, cancel, and check the transaction data. Many wallets show the raw transaction or contract being invoked. On one hand that can look cryptic, though actually decoding it with block explorers or dev tools clarifies intent. Work through contradictions: yes, crypto can be technical, but you don’t need to be a developer to be safe.
Phishing extensions. Fake store listings. Malicious dApps. Those are the big three. A fake extension will try to mimic icons and descriptions. Look at the publisher name, reviews, and install count. If anything smells fishy, close the tab. Wow, seriously—trust your gut here. If your instinct says “somethin’ off”, heed it.
Seed phrase scams are brutal. No legit wallet will ever ask for your seed phrase after setup. If a support agent, a website, or a popup asks for that 12 or 24‑word phrase, it’s a scam. Period. Don’t do it. Also, never enter your seed into a website form. Ever. Keep that phrase offline where possible. Store redundant copies in secure, separate places (e.g., a fireproof safe plus a secondary location).
Permissions creep is subtle. Some dApps request blanket approvals for recurring signatures. Don’t accept blanket approvals unless you fully trust the dApp. Approving repeated authority gives attackers a wider window to act if the dApp or your account is compromised. On the flip side, frequent signing is annoying; so weigh convenience vs. exposure. I still prefer to approve per-transaction, though I’m not 100% militant about it for tiny, low-stakes interactions.
Pin the extension to your toolbar. It saves time. Use separate browser profiles for trading and casual browsing. This keeps risky browsing habits away from your wallet. Seriously—it’s like having separate pockets for cash and receipts. My workflows got cleaner once I split profiles.
Enable wallet locks and auto-lock timers. Set a short idle timeout. That prevents accidental approvals when you step away. If you plan to interact with high‑value dApps, connect via a dedicated profile with only the wallet extension installed. (Oh, and by the way: clear cached site data sometimes.)
Check transaction history in SOL terms and token amounts, not just USD. Prices fluctuate. Looking at tokens helps you avoid confusion. Also, if a gas fee or processor fee looks unusually high, pause. Compare with recent similar transactions on a block explorer.
If you’re handling large sums, use a hardware wallet as the default. If you need enterprise-level custody, use institutional solutions with multi‑sig. If you suspect your machine is compromised (weird extensions installed, odd popups), don’t use the wallet until you clean the environment. On one hand a browser wallet is great for fast UX; on the other hand it’s not a vault for life savings.
Also, stay cautious around token approvals for unknown smart contracts. Some tokens have transfer hooks that can drain approvals in unexpected ways. If a token looks new and no audits exist, treat interactions as high risk. Repeat: audits help, but they are not guarantees. Audits reduce surface area for bugs, though actually they don’t eliminate human or economic incentives for exploits.
A: Phantom is widely used and has undergone security reviews. That said, safety depends on your behavior. Use verified download sources, protect your seed phrase offline, consider hardware for high-value holdings, and watch dApp permissions closely. Trust but verify.
A: Yes — with your seed phrase. Restore the phrase in a fresh install or on a different device. If you lose the phrase but still have access to an unlocked wallet, export the secret key immediately (then store it securely) or transfer funds to a new wallet whose recovery phrase you control. Careful: exporting keys increases risk, so do it only on a secure machine.
A: Immediately disconnect the wallet from the dApp, revoke approvals where possible, and move funds to a new wallet if you suspect compromise. Check the transaction history for unauthorized activity. Report the phishing attempt to relevant platforms and consider wiping the machine if malware is suspected. I’m not 100% sure every step will solve every case, but these steps reduce damage quickly.



